Thestrategist.media – 07 May 2015 – Forbes staff, Thomas Fox-Brewster reports that only “lines of code” managed to “bypass” Google’s alert service, namely “Google’s Password Alert service” that was launched in the beginning of last week sometimes.
On Wednesday, 29 April 2015, the official Google Blog warned the users from the looks of the “phishing” pages wherein “attackers” set a trap for stealing the password of respective users; as the latter type in their credentials the former retrieve the same in order to “gain access” to their respective “Google Account” without the knowledge of the consumers. Moreover, almost two percent of “messages to Gmail are designed” for the same purpose.
Furthermore, good phishing attacks succeed almost 45% of the times. Consequently, the protection of the customers’ accounts has become an issue of importance whereby Google announced the launch of “Password Alert”. Google informed that “Password Alert” is:
On Wednesday, 29 April 2015, the official Google Blog warned the users from the looks of the “phishing” pages wherein “attackers” set a trap for stealing the password of respective users; as the latter type in their credentials the former retrieve the same in order to “gain access” to their respective “Google Account” without the knowledge of the consumers. Moreover, almost two percent of “messages to Gmail are designed” for the same purpose.
Furthermore, good phishing attacks succeed almost 45% of the times. Consequently, the protection of the customers’ accounts has become an issue of importance whereby Google announced the launch of “Password Alert”. Google informed that “Password Alert” is:
“... a free, open-source Chrome extension that protects your Google and Google Apps for Work Accounts. Once you’ve installed it, Password Alert will show you a warning if you type your Google password into a site that isn’t a Google sign-in page.”
In fact, “Password Alert”, besides sending protective alerts, “encourages” the users to follow a healthy security practice of using “different passwords for different sites”. The said security system notifies the account holders as and when they type in their credentials “into a site that isn't a Google sign-in page”, thus the users can “update” their password to strengthen their accounts’ security.
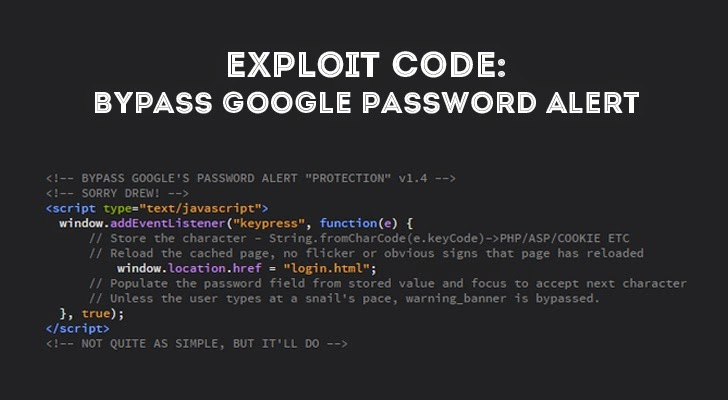
Interestingly, according to Brewster, the ‘security-expert’, Paul Moore, managed to break into “the Chrome browser extension” with the help of “some simple JavaScript that would kill alerts as soon as they started to appear”. Moore proved his case by first typing in his credentials in “a Gmail login page” without his “evil JavaScript” which showed the security alert. Subsequently, he performed the same action with the inclusion of his JavaScript code whereby the alert didn’t show up.
Moore’s code ran a check once in “every five milliseconds” which detected the “warning banner(s)” and destroyed the same “as soon as it was launched”. In Moore’s words:
“As it fires so rapidly, the alert appears and disappears too quickly to be detectable by the user. In short, anyone looking to launch a phishing attack against a Google account simply needs to add those seven lines to render the Password Alert protection useless… It’s an embarrassment really.”
However, Per Thorsheim, a password-expert, encouraged “consumers or businesses” to try out Google’s “Password Alert” tool for a “risk analysis”. He sees the said tool as “a novel idea from Google”, although it needs further development as currently “...it doesn’t look good.”
Google didn’t provide any comment when approached for the same issue, although it seems to have “fixed the issue with version 1.4, according to Google engineer Drew Hintz”. Nevertheless, there are still “other possible problems with the technology” as pointed by security experts whereby potential “brute force attack(s)” can be launched. A “malicious page” generating “fake keystrokes on behalf of the user” could then aim the appearing “warning banner”.
Consequently, Google’s protective tool is vulnerable to “malicious hackers” who can exploit the said security tool.
References:
http://www.forbes.com/sites/thomasbrewster/2015/05/01/google-embarassment-over-password-alert-hack/
http://googleblog.blogspot.co.uk/2015/04/protect-your-google-account-with.html